Key Insights
Australian businesses now need advanced Email & Collaboration security solutions to defend against fast-evolving cloud-based attacks.
- Email is still the biggest target for cybercriminals
- Collaboration platforms (Teams, Slack, OneDrive, Google Drive) are now equally exploited
- AI-generated phishing and impersonation attacks are rising sharply
- QR-code (quishing) and file-sharing attacks bypass basic filters
- Legacy SEGs don’t work effectively in cloud environments
- API + Inline hybrid protection is now the new standard
- Strong visibility, compliance and behavioural analysis are essential
Email has become the most targeted communication channel for Australian organisations. As cyberattacks continue to advance, attackers now exploit collaboration tools, cloud-based inboxes and user behaviour far more aggressively than they did just a few years ago. This shift has made it essential for businesses to adopt advanced, AI-powered, cloud-native Email & Collaboration security solutions that protect more than just inboxes.
Today’s threats move across the entire collaboration ecosystem—Microsoft 365, Google Workspace, Teams, Slack, OneDrive, SharePoint and shared files.

Modern Attacks Demand Modern Protection
During a recent technical discussion with Check Point Harmony security professionals—one message stood out: email threats are evolving faster than legacy tools can respond.
Phishing, impersonation attempts, insider risks and AI-generated attacks now outpace traditional gateways and filters, making Check Point Harmony Email & Collaboration (HEC) one of the most resilient Email Security Solutions for cloud environments.
This article dives deep into how email protection has evolved, why legacy tools fail in cloud-native setups, how Harmony Email & Collaboration’s hybrid architecture delivers stronger defence and the full breakdown of product SKUs designed for Australian businesses looking to upgrade to enterprise-grade Email & Collaboration security solutions.
Why Email Security Must Evolve – Insight Modern Threat Mechanics
Even though businesses have moved many workflows into productivity suites, file-sharing tools and collaboration platforms, email still drives the majority of communication. However, cloud inboxes and collaboration apps have exposed new gaps that attackers exploit aggressively. This is why next-generation Email & Collaboration security solutions must address far more than email filtering—they must protect entire digital workspaces.
Current Email Threats Include-
- AI-generated phishing designed to mimic human writing
- QR-code–based attacks (Quishing) that bypass link scanners
- Deepfake impersonation threats against executives
- Malicious file-sharing links (OneDrive, Google Drive, Dropbox)
- OAuth-based account takeover attacks
- Malware hidden in message bodies without attachments
- Delayed weaponisation (clean email becomes malicious post-delivery)
- Insider threat exploitation
- Social engineering supported by publicly available AI models
Legacy SEGs (Secure Email Gateways) and traditional Email Security Solutions cannot identify these behaviours effectively because they operate outside the cloud environment. Australian organisations now need Email & Collaboration security solutions that operate inside the ecosystem itself.
Technical Evolution – SEG vs Inline API vs Hybrid API + Inline
Understanding how email security has matured is essential for IT leaders selecting modern solutions.
1. Secure Email Gateways (SEGs) – The Legacy Model

In the early days of enterprise email, SEGs were sufficient. They sat outside the environment and re-routed email via MX record manipulation. Paul described this as “placing a mailbox at the front gate instead of delivering mail directly to the door.” This architecture creates inherent limitations:
Technical Issues with SEGs-
- No visibility into internal email flow
- No access to collaboration platforms
- Ineffective against cloud-specific attacks
- Slow updates and latency issues
- No behavioural or contextual analytics
- Inability to stop post-delivery threats
This is why SEGs are no longer considered modern Email & Collaboration security solutions.
2. Inline API Email Security
This approach inspects emails during the delivery flow without re-routing traffic. It provides faster inspection than SEGs and supports basic cloud-native integration.

However-
- Inline systems cannot analyse messages after delivery
- They do not review internal mailbox activity
- They lack full historical scanning capabilities
Inline API systems are a step forward—but still not “complete” Email Security Solutions.
3. Post-Delivery API Email Protection
API-based solutions plug directly into Microsoft 365 or Google Workspace and extract data after delivery. They offer deeper visibility, behavioural modelling and internal email scanning.
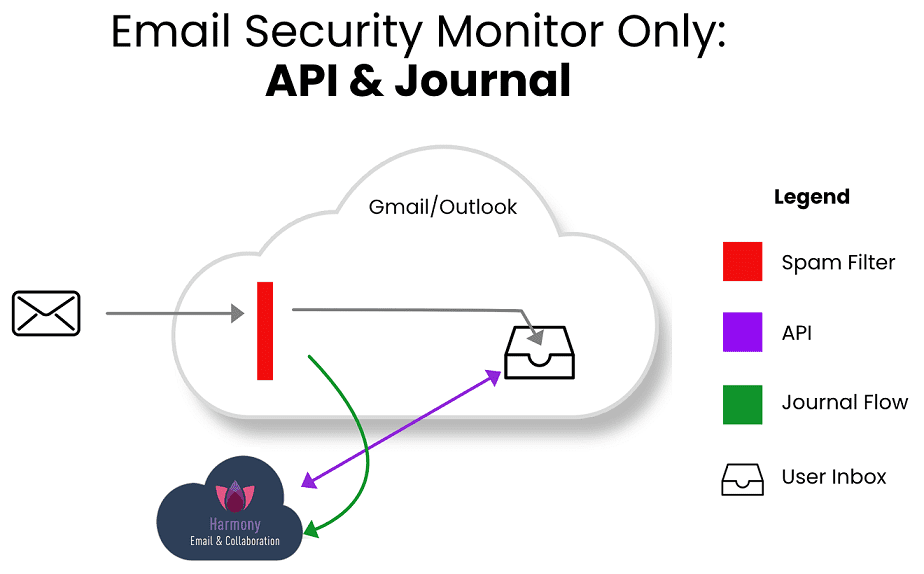
However-
- They cannot block threats before inbox delivery
- Sophisticated attacks may still enter the user’s mailbox
On their own, API-only tools are insufficient for comprehensive Email & Collaboration security solutions.
4. Check Point Harmony’s Hybrid Architecture- Inline + API
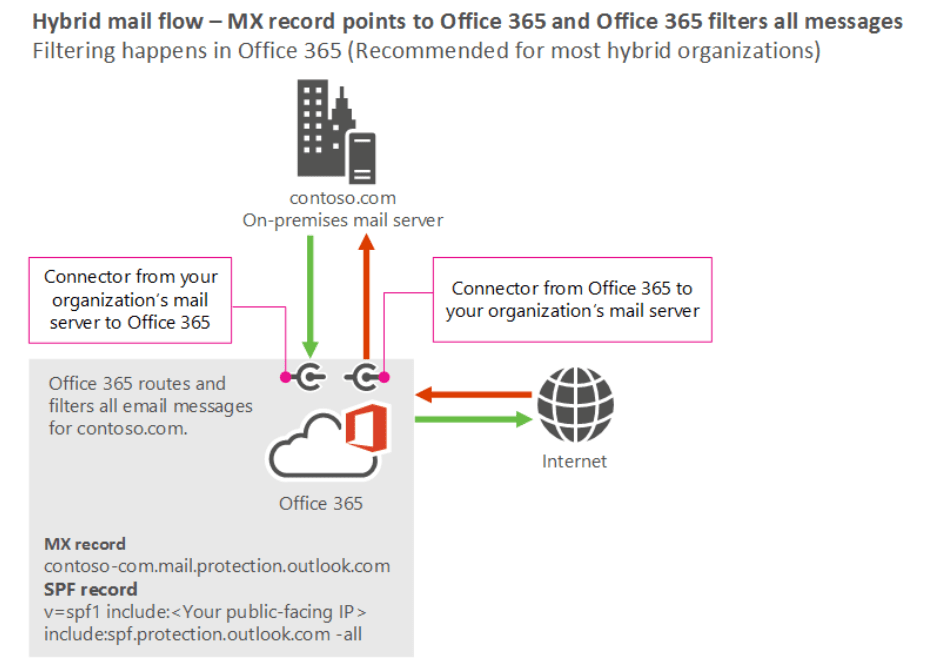
HEC is one of the only solutions that combines:
- Inline pre-delivery scanning
- API post-delivery visibility
- AI-powered detection & remediation
- Behavioural and identity-based analysis
This hybrid approach eliminates the weaknesses of SEGs, inline-only and API-only Email Security Solutions, providing total protection before, during and after message delivery.
Inside Check Point Harmony Email & Collaboration: A Technical Deep Dive
Harmony Email & Collaboration is built specifically for cloud environments. It integrates with Microsoft 365, Google Workspace, Slack, Teams, SharePoint, OneDrive and Google Drive. Below is the technical architecture breakdown.
1. Pre-Delivery Threat Prevention
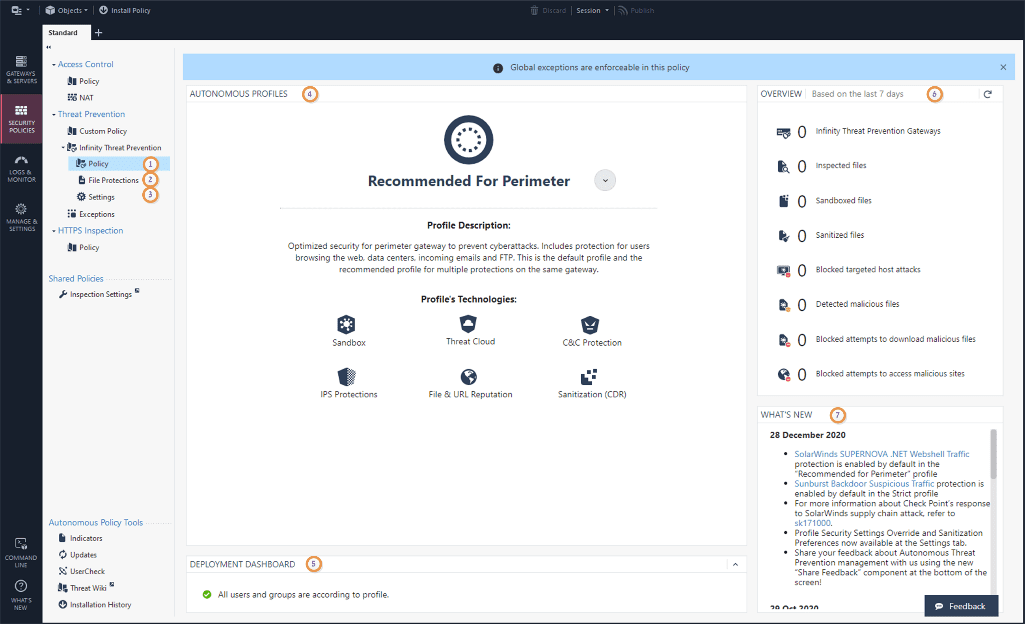
Before an email reaches an inbox, HEC scans-
- URLs and QR codes
- Attachments
- Sender identity
- Header anomalies
- Linguistic patterns (for impersonation)
- Domain reputation
- Message structure and behaviour
This proactive layer prevents phishing, malware, spoofing and impersonation attempts before the user ever sees them—unlike many traditional Email Security Solutions.
2. API-Based Deep Post-Delivery Analysis
If a threat bypasses pre-delivery scanning, the API engine conducts-
- Mailbox scanning
- Historical comparison
- Lateral movement detection
- Account takeover investigation
- Automatic message recall
- Forensic reporting
- Remediation actions based on policy rules
This gives organisations full visibility, something legacy Email & Collaboration security solutions do not provide.
3. AI-Powered Threat Detection with ThreatCloud AI

One of the strongest aspects of HEC is its integration with ThreatCloud AI, which processes 6 billion threat verdicts per day.
Technical capabilities include:
- Zero-day malware identification
- Behavioural modelling
- Language pattern analysis
- Attachment sandboxing
- Real-time global threat correlation
- Adaptive machine learning
This makes Harmony one of the most advanced Email security solutions for detecting emerging threats.
4. Collaboration Suite Protection
HEC extends beyond email into-
- Microsoft Teams
- Slack
- OneDrive
- SharePoint
- Google Drive
- Google Chat
- Dropbox integrations
HEC scans files, links, shared messages and collaborative interactions—giving businesses a unified Email & Collaboration security solution across platforms.
5. Compliance, Governance and Auditability
HEC supports Australian industry requirements with-
- Audit logs
- Full forensic trails
- Role-based access controls
- Compliance reporting (ISO, SOC, APRA, ACSC)
These capabilities allow businesses to maintain strong compliance posture—an essential requirement for banks, healthcare, government agencies and regulated environments that rely on complete Email & Collaboration security solutions.
How HEC Delivers Technical and Operational Advantages
- Seven-click deployment… no MX records changed
- 99.8% threat prevention rate
- Multi-platform coverage beyond email
- AI/ML-driven behavioural analysis
- Zero-day sandboxing
- URL & QR-code rewriting
- Auto-remediation & message recall
1. Cloud-native speed & visibility
These capabilities place Harmony far ahead of most competing email security solutions.
Product Breakdown: Check Point Harmony Email & Collaboration SKUs
Below is an accurate technical explanation of each SKU you provided.
1. Check Point Harmony – Email & Collaboration Protection (1–499 Seats)
SKU: CP-HAR-EC-PROTECT-EMAIL-T1-Y
Designed for small-to-mid-sized businesses needing enterprise-grade Email & Collaboration security solutions.
Includes-
- Full hybrid inline + API scanning
- AI/ML threat detection
- Microsoft 365 & Google Workspace integration
- Collaboration app security
- Attachment sandboxing
- URL/QR rewriting
- Automated post-delivery cleanup
➤ Request a quote for CP-HAR-EC-PROTECT-EMAIL-T1-Y
2. Check Point Harmony – Email & Collaboration Protection (500–4999 Seats)
SKU: CP-HAR-EC-PROTECT-EMAIL-T2-Y
Supports medium to large organisations with increased scalability.
Includes everything in T1 +
- Advanced impersonation modelling
- Tiered policy management
- Extended forensic visibility
- Multi-site configuration
- Integration with SIEM/SOAR platforms
Ideal for distributed environments requiring stronger technical controls and policy separation, making it one of the strongest mid-tier Email Security Solutions available.
➤ Request a quote for CP-HAR-EC-PROTECT-EMAIL-T1-Y
3. Check Point Harmony – Email & Collaboration Protection (5000+ Seats)
SKU: CP-HAR-EC-PROTECT-EMAIL-T3-Y
Enterprise-grade solution designed for large-scale, high-security environments.
Includes-
- Multi-tenant administration
- Extended AI-driven threat intelligence
- Global visibility dashboards
- Advanced automation and remediation
- Full forensic replay
- Enhanced SLA-based support
This tier offers maximum enterprise resilience for organisations requiring robust Email & Collaboration security solutions and global integration capability.
➤ Request a quote for CP-HAR-EC-PROTECT-EMAIL-T3-Y
How TECHOM Systems Delivers Value for Australian Businesses

TECHOM Systems offers a streamlined online store where Australian businesses can quickly purchase and activate robust Email & Collaboration security solutions from Check Point. Every product page clearly lists available SKUs, licence tiers and add-on services—making it simple to select, buy and deploy advanced Email Security Solutions without delays.
What our online store delivers-
- Easy SKU selection for T1, T2 and T3 licence bands
- Bulk licence ordering with transparent checkout
- Add-on options for deployment, configuration and ongoing optimisation
- Instant licence provisioning and activation guidance
- Policy templates aligned with Australian cybersecurity requirements
- Secure payments, GST-ready invoicing and full order history
Go for your licence, add configuration or management services and complete your order in minutes, your robust Email & Collaboration Security Solutions are ready to deploy as soon as checkout is complete.
Frequently Asked Technical Questions
1. Can Harmony detect AI-generated impersonation and CEO fraud attacks?
Yes. Harmony uses generative-AI linguistic analysis, identity modelling, sender reputation data and behavioural context to identify AI-generated phishing and deepfake impersonation attacks.
2. Does HEC protect internal email traffic and collaboration channels?
Yes. Harmony scans internal mailbox activity, Teams and Slack messages, file-sharing events and shared workspace actions—providing complete Email & Collaboration security solutions beyond the inbox.
3. How does Harmony stop zero-day threats?
Using ThreatCloud AI, sandboxing, behavioural analysis and signature-less detection—allowing Harmony to stop previously unseen malware before user exposure.
4. Will deployment affect business operations or email flow?
No. Deployment requires no MX record changes and completes in approximately 30 seconds. Harmony integrates directly through API, ensuring zero downtime.
5. Which SKU should my organisation select?
- T1: Up to 499 users
- T2: 500–4999 users
- T3: 5000+ users
All tiers include the full Email & Collaboration security solutions feature set, with differences only in scalability, administration and enterprise reporting.
Ready to Secure Your Email & Collaboration Environment?
Australian organisations can access the full range of Harmony Email & Collaboration licences designed for different team sizes-
- Harmony Email & Collaboration — 1 to 499 Users
SKU: CP-HAR-EC-PROTECT-EMAIL-T1-Y - Harmony Email & Collaboration — 500 to 4,999 Users
SKU: CP-HAR-EC-PROTECT-EMAIL-T2-Y - Harmony Email & Collaboration — 5,000+ Users
SKU: CP-HAR-EC-PROTECT-EMAIL-T3-Y
➞ Request a quote for any Harmony Email & Collaboration SKU
If you have a specific requirement or want clarity on the right solution to purchase, share what you need here… our team will guide you immediately.








